As businesses struggle with data protection and regulatory compliance, they often face limited, high-cost solutions to secure data ownership and utility. At the same time, users demand and deserve more
control and ownership over their data and intellectual property. The Midnight network seeks to address these challenges by creating a programmable privacy platform that balances data protection with operational flexibility. In this article, we explore how Midnight helps resolve the business challenge of choosing between
data protection, ownership, and utilization.
If you’re new to the Midnight network, here’s a primer on how Midnight helps secure and manage personal data on Cardano.
Addressing Core Issues in Data Security with the Midnight Network
Today, developers often face challenges when choosing secure data management solutions that also enable them to build scalable applications. Midnight, a new generation of blockchain technology, enables the development of apps that protect user, commercial, and transaction metadata.
Midnight is built on a zero-knowledge (ZK) framework, that allows selective data utility without compromising data protection, ownership, or user privacy. This technology allows businesses to design innovative applications, protect user data, and avoid exposing unnecessary customer information.
Wondering how apps built on Midnight differ from regular dApps? Let’s take a closer look:
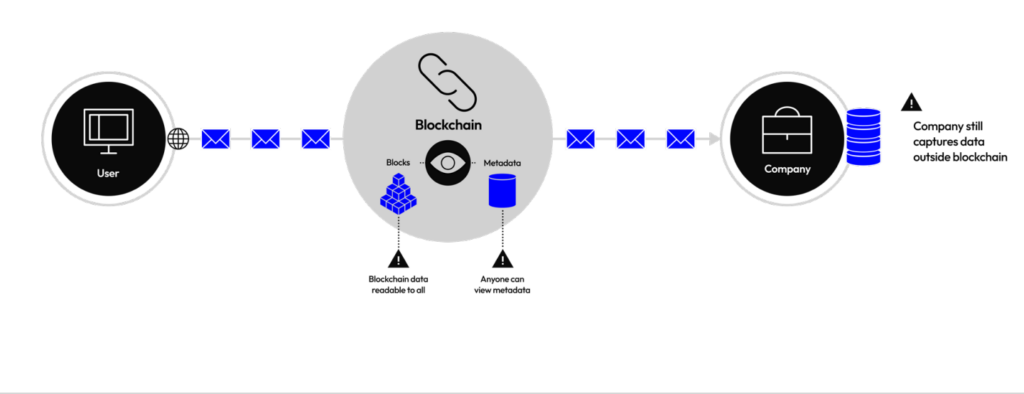
In a regular public chain dApp, we send sensitive data with public metadata that anyone can view and correlate to find more information about your activities.
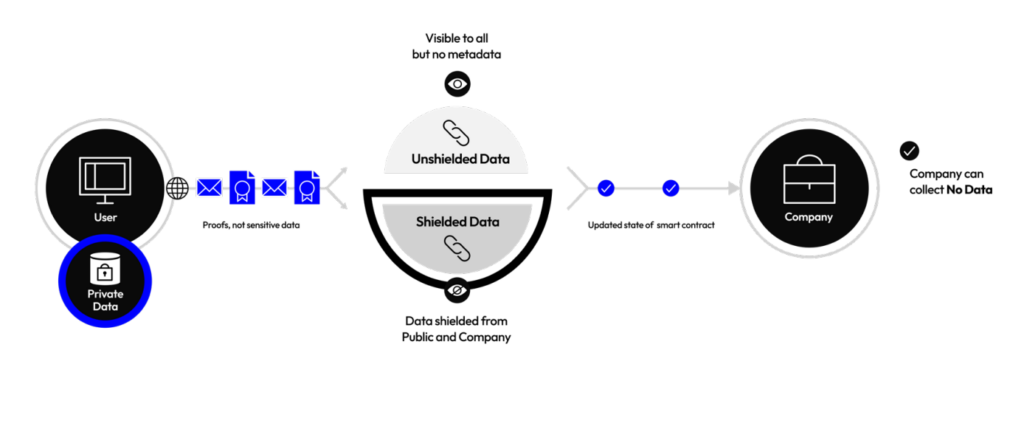
On the other hand, when you use Midnight to build a dApp, Midnight shields your data using proofs such that no metadata is created online unless you choose it to be on the public ledger.
Below are some key features and foundational principles that the Midnight-Network is architected using:
Privacy-First Architecture
Midnight uses TypeScript-based smart contracts for seamless developer integration, eliminating the need for niche programming skills. With ZK proofs embedded within the network, applications benefit from robust data protection and secure, efficient data attestation without revealing sensitive information.
Flexible Use for Developers and Operators
Midnight supports both shielded and unshielded data, allowing for selective data disclosures based on regulatory needs. The ledger’s TypeScript API design also supports smooth integration with existing systems, while its ZK architecture enables significant scaling through Kachina-based technology.
Seamless Interoperability
Midnight is designed to function as either a Layer 1 or Layer 2 blockchain, making it compatible with other networks such as Ethereum and Cardano. Its advanced ZK architecture uses the Halo2 cryptographic framework with innovative Pluto-Eris curves, supporting trustless interoperability for hybrid blockchain applications.
Use Cases for Midnight
Midnight is ideal for any use case requiring data and/or metadata protection. Its distributed ledger architecture increases data security and enables self-custody. Aditionally, the ZK capabilities enable scenarios where attestation about the underlying data is required without revealing the actual information to the querying party. These features are essential in use cases such as:
- Secure Voting Systems: Midnight’s privacy-first design makes it ideal for voting applications. Organizations can implement secure, fraud-resistant voting that verifies participant eligibility without tracking individual votes.
- Digital Identity Verification: Midnight provides a secure platform for identity verification, enabling KYC processes that protect user data. For example, a decentralized exchange (DEX) could verify age or credentials without revealing unnecessary personal details.
- Asset Tokenization: Midnight facilitates the tokenization of real-world assets like real estate, art, and more, storing ownership details on-chain without exposing personal data. This innovation paves the way for asset-backed economic models.
Unique Token Utility: NIGHT and DUST
Midnight uses a dual-token system with NIGHT and DUST tokens, each serving specific purposes to sustain the network’s functionality and privacy.
- NIGHT Token: As the network’s governance token, NIGHT facilitates consensus participation and incentivizes block production. It is a deflationary, unshielded token, ensuring easy liquidity and regulatory compliance.
- DUST Token: DUST is a shielded, decaying resource that acts as transaction energy. By shielding transaction metadata, it helps prevent data correlation and ensures predictable transaction costs, aligning with compliance requirements.
This dual-token approach allows Midnight to balance liquidity with privacy, making it one of the few blockchain platforms to prioritize regulatory resilience alongside technological advancement.
Developer-Friendly Architecture and Tools
Midnight’s architecture prioritizes ease of use and flexibility. Using TypeScript, the network supports developer onboarding through:
- Lightweight Compact Language: This language segregates the data layer from the application layer, allowing for smart contract functions without heavy cryptographic knowledge.
- Zero-Knowledge SNARKs: Midnight’s contracts enable privacy-focused transactions, with ZK proofs ensuring that only relevant information is shared.
- Comprehensive Developer Tools: Midnight’s documentation and APIs allow for seamless application development and deployment, removing the need for developers to master ZK technology.
Ecosystem Structure and Incentives
Midnight offers incentives for a wide range of participants:
- Developers: Midnight’s TypeScript structure minimizes the learning curve, while extensive documentation expedites application deployment.
- Block Producers: The network offers NIGHT token rewards to validators, with an initial pool of producers coming from Cardano’s stake pool operators (SPOs).
- App Operators: Midnight enables compliance through tools for programmable data protection, allowing businesses to audit certain activities without exposing underlying data.
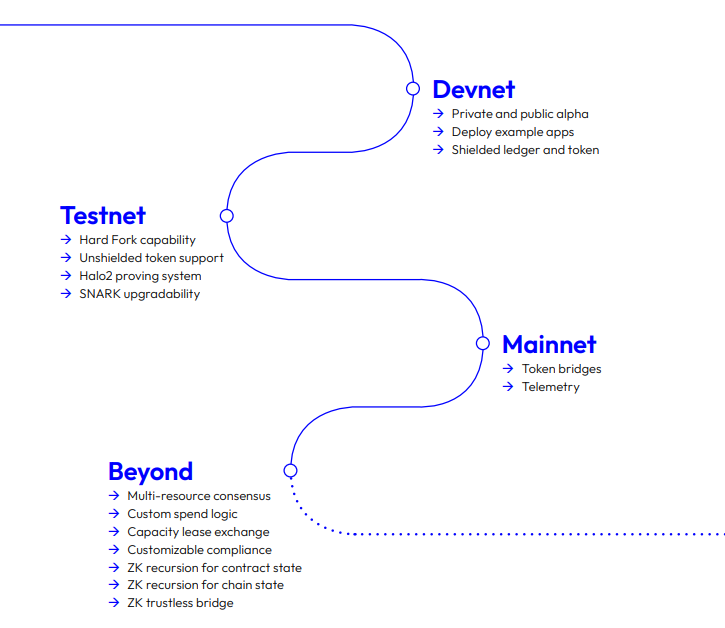
Development Roadmap
- Devnet: Initial alpha phases with shielded ledger and token integration.
- Testnet: Adding unshielded token support and Halo2 proving systems.
- Mainnet: Incorporating token bridges and telemetry.
- Beyond mainnet release: Plans for multi-resource consensus, customizable compliance, and ZK trustless bridges.
Accelerating ZKP dApp Development Through Partnerships

Most recently, the Midnight Network announced a strategic partnership with with Maestro, Paima Studios, and Sindri to bring enhanced tooling for for developers building zero-knowledge applications. The tooling include powerful data APIs, EVM endpoint support, and increased proving times. According to Eran Barak, the CEO of midnight, these new collaborations will enable quicker development and adoption of data-protecting dApps.
Here’s what other partners said about this collaboration:
Maestro through Marvin Bertin, the co-founder and CEO: “Midnight addresses a major gap in the blockchain market, with the potential to unlock an entirely new set of use cases. We’re excited to be working with their team to help accelerate adoption and ecosystem growth by making the development experience as intuitive as possible.”
Paima Studios through their co-founder Sebastien Guillemot: “Midnight is an early player in bringing a new class of cryptographic techniques to life and I think that, combined with the founding team’s track record, it has a lot of potential to become something great. This collaboration has the potential to give millions of developers access to not only Midnight’s data protection solutions, but blockchain more broadly.”
Sindri through Stasia Carson, the CEO and co-founder: “For zero-knowledge technology to thrive, developers need accessible, modern tools that integrate seamlessly into their workflows. Through our collaboration with Midnight, we’re fulfilling this vision while enabling organizations to develop privacy-first applications that meet regulatory standards and ensure users retain control over their personal data.”
Putting it all together
Midnight’s innovative use of privacy-preserving technology is unlocking programmable data protection capabilities that balance on-chain transparency with evolving data handling and compliance mandates. By integrating ZK proofs and a developer-friendly approach, Midnight makes blockchain more accessible for businesses while maintaining regulatory compliance. As it continues to develop, the Midnight Network is a game-changing platform for anyone looking to build secure, scalable, and compliant dApps with zero-knowledge capabilities.
For more information, visit the official midnight.network website or join the conversation on Discord and Twitter.