Blockchain technology has made significant strides since its inception, transforming the financial technology (FinTech) landscape with its revolutionary approach to data management and transactions. The concept of a blockchain was first introduced in 2008 by the anonymous creator(s) known as Satoshi Nakamoto, who launched Bitcoin as the first practical application of this technology.
The primary challenge that blockchain sought to address was the consensus problem, which arises when multiple parties need to agree on a single version of a shared digital history without relying on a central authority. Bitcoin solved this problem by implementing the Proof-of-Work (PoW) consensus algorithm. PoW relies on the computational power of participating nodes to validate and record transactions on a decentralized, tamper-proof ledger.
The core proposition of blockchain technology is “security via decentralization.” By distributing the responsibility of maintaining the network’s integrity among multiple nodes, the system becomes more resistant to attacks and manipulation. This decentralization ensures that no single entity has control over the network, thus promoting trust and transparency.
2. Understanding Blockchain Decentralization: A Stratified Approach
To gain a comprehensive understanding of blockchain decentralization, we must first recognize that it is a multifaceted concept. By stratifying blockchain systems into multiple layers, we can better analyze the security properties and decentralization characteristics of each layer independently. This section introduces the methodology used to examine these layers and assess the overall decentralization state of a blockchain system.
The stratification of blockchain systems can be broadly divided into six layers:
Hardware Layer: This layer involves the computational devices used in validating transactions and securing the network. Decentralization is achieved by promoting diverse mining devices and preventing mining power concentration, ensuring overall system security and integrity.
Network Layer: This layer is responsible for the communication between nodes and the distribution of transaction data. Security properties of interest at this layer include network resilience, censorship resistance, and fault tolerance.
Consensus Layer: The consensus layer deals with the agreement among nodes on the state of the blockchain. Key security properties include consensus safety, resistance to Sybil attacks, and resistance to long-range attacks.
Application Layer: This layer comprises smart contracts and decentralized applications (dApps) built on top of the blockchain. Security properties of interest include contract safety, privacy, and upgradability.
Governance Layer: Governance is vital for the long-term success and stability of blockchain systems. Effective governance ensures that the ecosystem adapts to changing needs, resolves conflicts, and allocates resources efficiently. The key categories of governance to consider are conflict resolution and development funding, both of which contribute to maintaining decentralization and promoting a sustainable blockchain ecosystem.
Geography Layer: Geography plays a significant role in the decentralization of blockchain systems, as factors such as physical safety and legal compliance can contribute to the overall resilience and robustness of these systems. By ensuring a diverse and distributed geographic landscape, we can enhance the decentralization and resilience of a blockchain system.
3. Hardware
Blockchain systems rely on various mechanisms to protect against Sybil attacks, where an adversary creates multiple fake identities to manipulate the consensus process. Two prevalent consensus algorithms, Proof-of-Work (PoW) and Proof-of-Stake (PoS), employ distinct methods to achieve Sybil resilience. In PoW systems, computational power serves as the primary resource for determining a node’s influence, while PoS systems utilize the amount of cryptocurrency held as collateral.
In PoW systems, mining hardware plays a crucial role, as it dictates the computational power available to validate transactions and secure the network. Over time, PoW systems have seen a shift towards specialized mining devices, such as Application-Specific Integrated Circuits (ASICs), which provide a significant performance advantage over general-purpose computers. This shift has led to centralization tendencies, as the production and distribution of mining hardware are controlled by a small number of companies.
This centralization of mining power presents several risks to the overall security and integrity of PoW systems. For instance, a few dominant manufacturers could potentially introduce collective faults or backdoors into the hardware, undermining the network’s security. Additionally, the concentration of mining power could lead to collusion among miners, making the network susceptible to 51% attacks or censorship attempts.
4. Network layer
The network layer is a critical component of blockchain systems, responsible for facilitating communication between nodes and disseminating transaction data across the network. To ensure the decentralization and security of a blockchain system, the network layer must exhibit three key properties: network resilience, censorship resistance, and fault tolerance.
Network Resilience: A resilient network can withstand node failures or attacks without significant disruption to its operation. To achieve this, the network must be designed with redundancy and diverse routing paths to prevent single points of failure.
Censorship Resistance: Censorship resistance ensures that no single party can control the flow of information or selectively prevent transactions from being included in the blockchain. A decentralized network design, with a large number of nodes, can help achieve this property.
Fault Tolerance: Fault tolerance enables the network to continue functioning correctly even in the presence of faulty or malicious nodes. This can be achieved through consensus algorithms that accommodate byzantine behavior and the implementation of robust error-detection mechanisms.
Despite the importance of these properties, centralization risks can still arise within the network layer. For example, reliance on centralized services, such as domain name systems (DNS) or cloud providers, can introduce vulnerabilities and undermine the system’s decentralization. Furthermore, internet infrastructure centralization, such as the concentration of internet exchange points or submarine cables, can also pose risks to the network’s resilience and censorship resistance.
To enhance decentralization at the network layer, several strategies can be employed. These include using peer-to-peer communication protocols, implementing overlay networks like Tor or the InterPlanetary File System (IPFS) to reduce reliance on centralized services, and fostering a diverse ecosystem of nodes with different hardware, software, and geographical locations.
5. Consensus layer
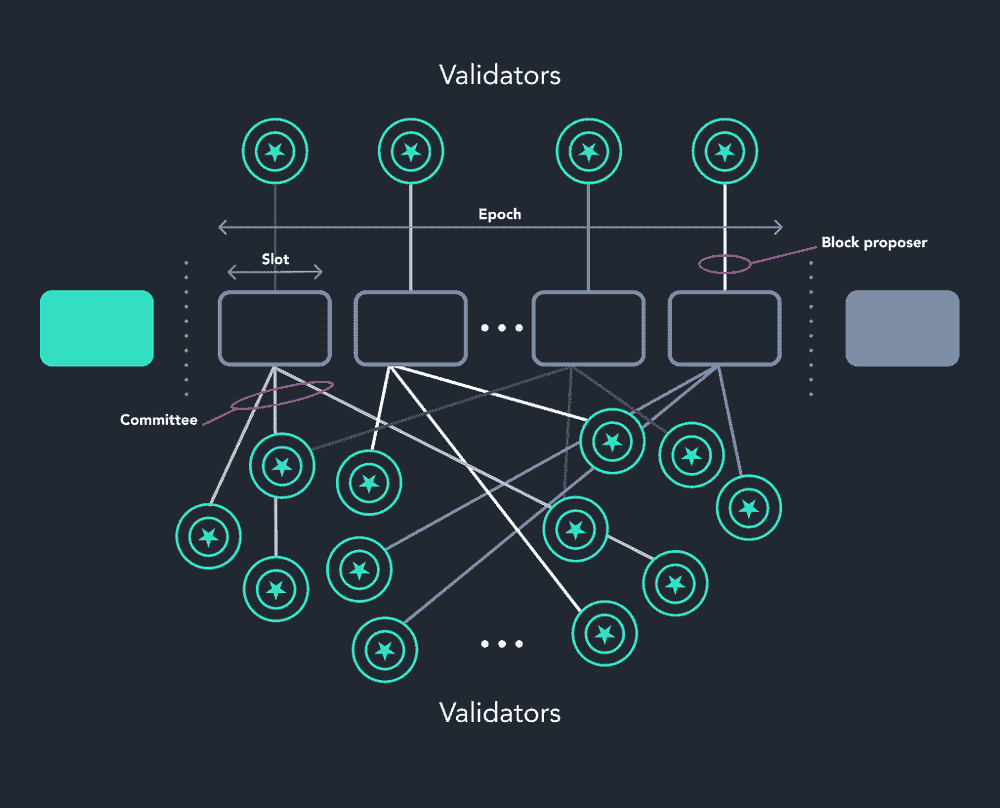
The consensus layer plays a pivotal role in blockchain systems, ensuring that all nodes agree on a single, consistent version of the shared ledger. To maintain decentralization and security at this layer, a blockchain system must exhibit consensus safety, resistance to Sybil attacks, and resistance to long-range attacks.
Consensus Safety: Consensus safety refers to the assurance that nodes will not accept conflicting versions of the ledger. This property is crucial for maintaining the integrity of the blockchain and preventing double-spending attacks. Both Proof-of-Work and Proof-of-Stake algorithms are designed to achieve consensus safety through economic incentives that discourage malicious behavior.
Resistance to Sybil Attacks: As discussed in before, consensus algorithms must be resilient against Sybil attacks, where an attacker creates multiple fake identities to manipulate the consensus process. Proof-of-Work and Proof-of-Stake systems utilize different resources (computational power and cryptocurrency holdings, respectively) to achieve this resistance.
Resistance to Long-Range Attacks: Long-range attacks occur when an attacker attempts to rewrite the blockchain’s history by creating an alternative chain from a point far in the past. Resistance to such attacks can be achieved by implementing checkpoints or through strong subjectivity in Proof-of-Stake systems, where new nodes rely on trusted information to synchronize with the network.
Centralization risks at the consensus layer vary depending on the consensus mechanism employed. In Proof-of-Work systems, centralization can result from the concentration of mining power, as discussed in Section 3. In contrast, Proof-of-Stake systems may experience centralization risks if a few large stakeholders control a significant portion of the network’s staking power.
To enhance decentralization at the consensus layer, several strategies can be employed. For Proof-of-Work systems, adopting more energy-efficient and egalitarian mining algorithms can reduce the barriers to entry for miners and promote a more diverse mining ecosystem. For Proof-of-Stake systems, implementing mechanisms that encourage stake decentralization, such as token distribution events or decentralized staking pools, can help mitigate centralization risks.
6. Application layer
The application layer encompasses smart contracts and decentralized applications (dApps) built on top of blockchain systems. As these applications serve as the primary interface for users, they play a crucial role in shaping the user experience and driving adoption. To ensure a robust and decentralized application layer, it is essential to focus on contract safety, privacy, and upgradability.
Contract Safety: Contract safety refers to the assurance that smart contracts will execute as intended without unintended consequences or vulnerabilities. Ensuring contract safety involves rigorous testing, code audits, and the use of formal verification techniques to minimize the risk of bugs and exploits.
Privacy: Privacy is a critical concern for users of blockchain applications. While public blockchains offer transparency, they can also expose sensitive user data. Implementing privacy-enhancing technologies, such as zero-knowledge proofs or confidential transactions, can help protect user privacy while maintaining the benefits of decentralization.
Upgradability: As software evolves, it is essential for smart contracts and dApps to be upgradable to incorporate improvements, fix bugs, or adapt to changing requirements. However, striking a balance between upgradability and immutability is challenging, as too much central control can undermine decentralization.
Centralization risks at the application layer can arise from reliance on third-party services or the concentration of development power. For example, dApps that depend on centralized oracles or data feeds can introduce single points of failure or manipulation. Additionally, a small group of developers or organizations dominating the development of popular dApps can pose risks to the ecosystem’s diversity and resilience.
To enhance decentralization at the application layer, several strategies can be employed. These include fostering a diverse developer ecosystem, using decentralized oracles and data sources, and implementing decentralized governance mechanisms that enable community input and decision-making. Encouraging open-source development practices and supporting grassroots projects can also contribute to a more decentralized and robust application layer.
7. Governance

Governance plays a vital role in the long-term success and stability of blockchain systems. Effective governance ensures that the ecosystem adapts to changing needs, resolves conflicts, and allocates resources efficiently. In this section, we will explore two key categories of governance: conflict resolution and development funding.
Conflict Resolution: Conflicts within a blockchain ecosystem can arise from various sources, such as disagreements over protocol upgrades or disputes between different stakeholders. Decision-making power is the crucial resource in conflict resolution, and all system entities, including users, miners, developers, and investors, should be considered relevant parties. Decentralized governance models aim to distribute decision-making power among these entities, preventing undue influence or control by a single group.
Development Funding: Sustaining and improving blockchain systems require ongoing development efforts, including bug fixes, feature enhancements, and research initiatives. Active developers are essential for driving innovation and maintaining the ecosystem’s health. However, funding these efforts can be challenging, as public blockchains often lack traditional revenue streams.
To address these challenges, various models of development funding have been proposed and implemented. Some examples include:
a. Block rewards or transaction fees: Allocating a portion of the block rewards or transaction fees generated by the network to fund development efforts.
b. Treasury systems: Establishing a dedicated treasury, funded by a percentage of newly minted tokens or other revenue sources, to support development and other ecosystem initiatives.
c. Decentralized autonomous organizations (DAOs): Utilizing DAOs to manage and distribute funds for development, allowing community members to vote on proposals and resource allocation.
Incorporating effective governance mechanisms in a blockchain system is crucial for maintaining decentralization and ensuring the ecosystem’s long-term sustainability. By balancing the interests of various stakeholders and providing a framework for resource allocation and decision-making, decentralized governance models can promote a more robust and resilient blockchain landscape.
8. Geography
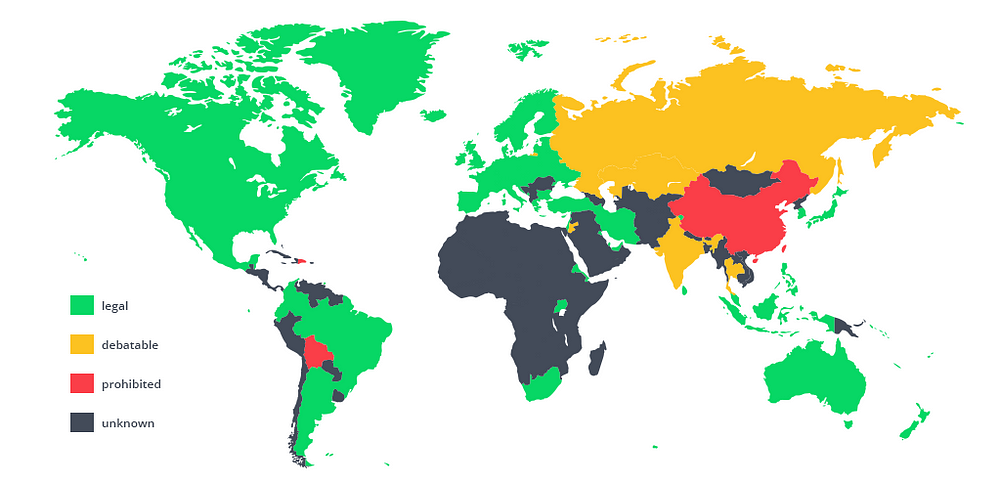
Geography plays a significant role in the decentralization of blockchain systems. By considering factors such as physical safety and legal compliance, geographic distribution can contribute to the overall resilience and robustness of these systems. In this section, we will explore the categories of geography in the context of blockchain decentralization.
Physical Safety: The geographic distribution of nodes, mining facilities, and other infrastructure components has a direct impact on the physical safety of a blockchain system. A decentralized system with a broad geographic distribution reduces the likelihood of single points of failure, such as natural disasters, power outages, or targeted attacks. Ensuring the physical safety of key resources, including hardware, network infrastructure, and consensus mechanisms, is critical for maintaining a secure and decentralized system.
Legal Compliance: The regulatory landscape for blockchain technology varies greatly across jurisdictions. Legal compliance is essential for the long-term sustainability of a blockchain system, as non-compliance can lead to sanctions, fines, or other restrictions that can hamper the ecosystem’s growth. Decentralization can help mitigate regulatory risks by distributing the system’s components across multiple jurisdictions, making it less vulnerable to adverse regulatory actions in any single country.
In the context of geography, all resources discussed in previous sections, such as hardware, network infrastructure, consensus mechanisms, and application layer components, are relevant parties in the system’s geographic design. Ensuring a diverse and distributed geographic landscape can enhance the decentralization and resilience of a blockchain system.
Considering geography is an essential aspect of decentralization can contribute to the overall security, resilience, and regulatory compliance of blockchain systems. By examining and addressing centralization risks across hardware, network, consensus, application, governance, and geographical layers, we can contribute to the development of more secure, resilient, and decentralized blockchain systems for the future.