In this article we’ll dive into the world of zero-knowledge proofs, discussing the differences between various types of proofs such as zk-SNARKs and zk-STARKs, while taking a deep dive into the fundamentals of zk-Rollups.
Moreover, we’ll examine the latest advancements in zk-technology across major blockchain platforms like Cardano, Ethereum & Tezos. We’ll explore how these platforms are incorporating zk-Rollups to boost their networks’ performance, scalability, and privacy.
We will be covering each L2 scaling solution, providing a deep dive into each of them. This article serves as an introduction to that.
Ok, let’s dive in👇
What is Zero-Knowledge Proof?
In simple terms, zk-Proof (ZKP) is a cryptographic technique that allows two parties to exchange information without revealing any sensitive data.
It’s a cryptographic technique proposed by MIT researchers Silvio Micali, Shafi Goldwasser, and Charles Rackoff in the 1980s.
This technique allows one party, known as the Prover, to prove a statement to another party, the Verifier, without revealing any additional information besides the fact that the statement is true.

It’s like proving you have sufficient income to your landlord without disclosing any financial information. In fact, Micali and Goldwasser were awarded the Turing Award for their outstanding contributions to cryptography.
Where’s Waldo?
Let’s explore how zero-knowledge proofs (ZKPs) work using the “Where’s Waldo” puzzle as an example. Waldo is a small figure hidden among various characters in a children’s puzzle book, and the objective is to find his location on each page.

In this scenario, we have two characters:
- Alice (the Prover)
- Bob (the Verifier)
Alice and Bob are playing “Where’s Waldo.” Shortly after the game begins, Alice claims to have found Waldo.

Skeptically, Bob asks her to prove it without revealing Waldo’s exact location. In response, Alice devises a simple zero-knowledge proof.
She finds an opaque card that is at least twice the height and width of the “Where’s Waldo” puzzle. Then, she cuts a Waldo-shaped hole in the center of the card, just large enough to reveal Waldo and nothing else.

By placing the card over the puzzle, Alice can show Bob that she knows where Waldo is without disclosing his exact position.

Through this zero-knowledge proof, Alice, the Prover, successfully convinces Bob, the Verifier, that she knows Waldo’s location without revealing any additional information about his whereabouts.
Types of zk-Proofs: Interactive and Non-Interactive
There are two types of zk-Proofs: interactive and non-interactive.

Interactive ZK-Proofs involve multiple rounds of interaction between the prover and the verifier, while non-interactive ZK-Proofs require no interaction between the two parties.

In a setting like an internet, where multiparty computation is involved, interactive zero-knowledge proofs have their disadvantages. These include:
- no concurrency,
- limited transferability,
- and limited scalability.
To address these issues, non-interactive ZKPs were developed. As the name suggests, non-interactive ZKPs (NIZKPs) require no interaction between the prover and verifier, and instead, use a hash function or digital signature as the verifier.
The hash function result becomes the challenge, and the proof can be represented as a single message instead of a multi-step interaction between the prover and the proof-checking entity.
So let’s look at the common types of non-interactive ZKPs👇
zk-SNARKs: Succinct Non-Interactive Arguments of Knowledge
zk-SNARKs are well-known NIZKPs that offer short proof sizes and fast verification times.
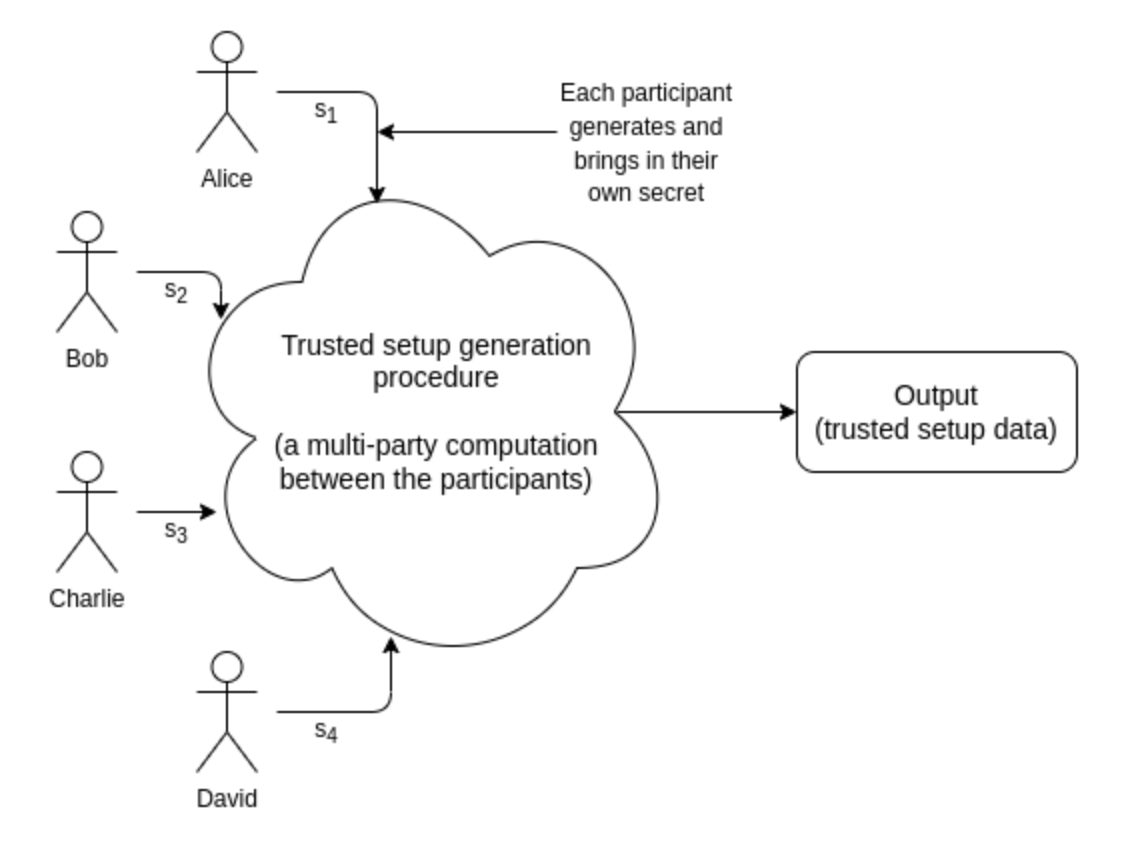
However, they usually rely on a trusted setup, making them potentially vulnerable to manipulation.
Widely adopted in privacy-focused blockchain protocols like Zcash and Layer 2 scaling solutions such as zk-Rollups, zk-SNARKs have seen significant advancements recently.
The Electric Coin Company introduced Halo, a new zk-SNARK protocol that eliminates the need for trusted setup ceremonies. Developed by engineer Sean Bowe, Halo addresses limitations in previous zk-proofing systems like BCTV 14 and Groth 16.
Halo’s innovative “Nested Amortization” technique collapses multiple proofs together over elliptic curve cycles, enabling computational proofs to reason about themselves efficiently. This eliminates the need for trusted setup ceremonies.
Bulletproofs
Bulletproofs was designed to provide short proofs with strong security assumptions. They use logarithmic proof sizes instead of linear ones, making them more scalable.
Bulletproofs do not require a trusted setup but use multiparty computation (MPC) instead, making them more reliable.
However, they are not post-quantum secure. Monero is an example of a cryptocurrency that has implemented Bulletproofs to reduce transaction sizes. Bulletproofs are also used in the Mithril protocol of Cardano.
zk-STARKs: Scalable Transparent Argument of Knowledge
zk-STARKs are transparent, trustless, and quantum-resistant NIZKPs created in 2018.
They do not rely on a trusted setup, making them more secure and scalable. zk-STARKs use collision-resistant hash functions instead of elliptic-curve cryptography, providing quantum resistance.
However, their proof sizes are significantly larger than those of zk-SNARKs, which can impact verification time.
StarkEx and StarkNet are examples of solutions using zk-STARKs.
Here’s a concise comparison of different types of NIZKPs:
As we have now understood the basics of zk proofs, let’s dig into the prominent use cases of zk- technology in the blockchain space 👇
What are zk-Rollups?
As of now, blockchains cannot match the efficiency and speed of centralized systems. ZK-rollups are touted as the future of blockchain scaling, bringing scalability to the blockchain space and making them competitive with centralized systems.
So, let’s take a look at the fundamentals of ZK-rollups and how they scale blockchains.
zk-Rollups are Layer 2 scaling solutions that move computation and state off-chain while storing transaction data on-chain on a Layer 1 blockchain.
They increase transaction throughput and reduce costs by periodically posting valid batches of transactions from the Layer 2 network bundled up to Layer 1, leveraging the base layer’s security and censorship resistance for settlement.

ZKPs are used to verify the correctness of the state changes proposed by Layer 2, demonstrating with mathematical certainty that these changes are the result of the execution of the given batch of transactions.
Zk-Rollups rely on the base layer for data availability, settlement, and censorship resistance, and their state is maintained by a smart contract deployed on the Layer 1 network. Layer 2 operators, such as centralized sequencers or proof-of-stake validators, execute transactions, bundle them up in batches, and submit the batch to the Layer 1 network.
The Current zk-Rollup Landscape
Ethereum and Tezos are the two blockchains that are at the forefront of developing zk-Rollups, which offer innovative solutions for enhancing scalability and privacy. Let’s dig into these two ecosystems and explore the recent developments in zk-Rollups.
The Ethereum zk-Rollup Ecosystem

1. Polygon zk-Rollups on Ethereum
- Polygon zkEVM introduced a zero-knowledge EVM (zkEVM) implementation. With Polygon zkEVM, developers can easily port Ethereum-based dApps to Polygon rollup or launch EVM-compatible dApps directly on the rollup.
- Polygon Miden:General-purpose, STARK-based ZK rollup with EVM compatibility, processing up to 5,000 transactions in a single block. Polygon Miden relies on the Miden Virtual Machine (VM) to execute arbitrary logic and run smart contracts, making it unique among STARK-based ZK rollups.
- Polygon Nightfall: Enterprise roll-up solution for private transactions, combining optimistic rollups and zero-knowledge cryptography. Developed in collaboration with Ernst & Young (EY), it aims to provide scalable and private blockchain transactions for large-scale companies.
2. StarkNet zk-Rollups on Ethereum
- StarkNet: zk-Rollup on Ethereum with Cairo programming language. Developers need to learn Cairo, although transpilers from Solidity to Cairo are being created to facilitate onboarding.
- StarkEx: SaaS scalability solution for decentralized crypto exchanges (DEXs), deployed on Ethereum since mid-2020. It supports ETH, ERC-20 tokens, and tokens on other EVM-compatible chains, as well as ERC-721 NFTs. StarkEx is used by dApps and protocols like dYdX, Immutable, DiversiFi, and Sorare.
3. zkSync
zkSync is an Ethereum Layer-2 scaling solution using SNARKs, with full EVM compatibility and 2,000+ TPS. It allows nearly instantaneous withdrawal of funds to the Ethereum Layer-1 mainnet and simplifies the process of redeploying live smart contracts from Ethereum.
4. Loopring
Loopring is a zk-Rollup on Ethjereum, that processes an average of 200 TPS. It enables non-custodial trading using order book methods, requiring less liquidity than automated market maker (AMM) technology.
5. Aztec
Aztec is a privacy-focused smart contract platform secured by Ethereum, utilizing SNARKs and PLONK algorithm. It plans to use its customized privacy-based programming language, Noir, based on Rust. The Noir testnet is coming online in Q4 2022, with the mainnet expected to follow soon after.
6. Immutable X
Immutable X: High-throughput Ethereum layer-2 scaling solution for NFT minting and trading, using ZK-SNARK technology developed by StarkWare. It can process 9,000 TPS and comprises three main parts: Immutable X platform, Immutable X marketplace, and Immutable X token (IMX).
Here’s a table that summarises the economic activity on these zk-rollups on Ethereum.

The Tezos zk-Rollup
- Epoxy: a Tezos-based validity rollup framework, sets itself apart from Ethereum-based zk-Rollups by being integrated as a first-class citizen within the Tezos economic protocol. This unique integration allows for the development of a diverse range of applications. Epoxy leverages aPlonK to achieve high TPS rates by aggregating multiple proofs. As Tezos’ zk-Rollup solution, Epoxy has made its way onto Mondaynet for testing.
As you can see, zk-Rollups have made significant progress in addressing Ethereum’s scalability issues.
Apart from scalability, zk technology has another use case in the blockchain space: privacy.
Privacy Landscape
ZKPs facilitate private transactions on blockchains such as Monero and Zcash. These privacy-centric cryptocurrencies leverage ZKPs to conceal transaction details, including sender and receiver addresses and transaction amounts, while maintaining a secure and verifiable network.
With this in mind, let’s look at the blockchains and projects leveraging the privacy aspect of ZKPs 👇
Monero
Monero is a privacy-focused cryptocurrency with a $2.6B market cap and 18.2 million circulating $XMR. It employs ring signatures and Ring Confidential Transactions (an advanced form that also uses stealth addresses) to facilitate private transactions.

Monero’s ring signatures create a group of possible signers to maintain plausible deniability and transaction output untraceability. Additionally, Monero uses the Pedersen commitment to hide transaction amounts, sender, and receiver addresses.
Monero initially used a variation of ring signatures for zero-knowledge range proving, but this method was inefficient. The introduction of Bulletproofs significantly improved the efficiency of range proofs.
Zcash
Zcash is a privacy-focused cryptocurrency with a $1.8B market cap and 12.9 million circulating $ZEC. It employs zk-SNARK to enable private transactions. Zcash’s zk-SNARKs allow users to maintain transaction confidentiality.

Zcash transactions can be transparent or shielded. Transparent transactions function like Bitcoin transactions, while shielded transactions utilize zk-SNARKs to hide transaction details, including sender and receiver addresses and transaction amounts. Zcash uses a combination of commitment schemes and ZKPs to ensure transaction privacy and prevent double-spending.
Cardano: The Midnight Sidechain

Midnight, an exceptional sidechain initiative built on the Cardano blockchain, prioritizes privacy and data security by employing ZKPs and confidential computation.
The project facilitates the creation of dApps without mandating user data disclosure, made possible by its privacy-centric blockchain architecture. It provides a tailored compiler, native support for ZK smart contracts, and a range of developer tools, enabling the utilization of the widely-used TypeScript programming language
To dive deeper into Midnight check out this Ada Pulse Articel.
Conclusion
Advancements in zero-knowledge technology are accelerating rapidly, presenting unique use cases in the blockchain domain, ranging from scaling solutions to privacy enhancements. Projects concentrating on zero-knowledge technology are certainly worth keeping an eye on, given their potential impact on the space.